Question On Network Security And Asked
Who should Practice these Network Security Based Quiz?
- Anyone wishing to sharpen their knowledge.
- Anyone preparing for aptitude test.
- Anyone preparing for interview.
In these quiz we Covers Following Topics:
- TCP/IP and Communication Networks
- Internet Protocol, Network Addressing and Transport Level Security
- Wireless Network Security and Network Security Overview
What you’ll learn
- Able to Solve Multiple Choice Questions on Network Security
- Students will develop a strong confidence on topic "Network Security"
Are there any course requirements or prerequisites?
- Basic knowledge of Computer Network
- Basic Knowledge of Electronics
Who this course is for:
- Students who want to Learn About "Network Security"
A device which is used to boost the signal between two cable segments or wireless access points is
A. Router
B. Repeater
C. Booster
D. Switch
Eplanation
The Correct Answer is B .
The correct term for such a device is a Repeater.
‘Jitter’ refers to:
A. variation in the packet arrival time
B. errorless delivery
C. timely delivery of message
D. non of the mentioned
Eplanation
The Correct Answer is A .
‘Jitter’ refers to variation in the packet arrival time.
IEEE 802.8 is/was:
A. Fiber Optic TAG
B. Wireless LAN and Mesh
C. IBM Token Bus
D. Integrated Services LAN
Eplanation
The Correct Answer is A .
IEEE 802.8 was the Fiber Optic TAG (disbanded).
Which is the smallest unit amongst the following with reference to the ATM:
A. virtual circuit
B. virtual path
C. transmission path
D. all are of the same size
Eplanation
The Correct Answer is A .
Virtual circuits are the smallest unit in the above options.
We need to send 265 kbps over a noiseless channel with a bandwidth of 20 kHz. How many signal levels do we need?
A. 128
B. 512
C. 256
D. 1024
Eplanation
The Correct Answer is A .
256000 = 2 × 20000 × log L = 6.625.
L = 98.7 Levels.
Since this result is not a power of 2, we need to either increase the number of levels or reduce the bit rate. If we have 128 levels, the bit rate is 280 kbps.
Which topology requires the most amount of wiring?
A. Ring
B. Bus
C. Star
D. Mesh
Eplanation
The Correct Answer is D .
This is the disadvantage of mesh topology.
Which topology has a central hub?
A. Bus
B. Mesh
C. Ring
D. Star
Eplanation
The Correct Answer is D .
The star topology has a single hub.
Calculate the theoretical channel capacity. If SNR(dB) = 36 and the channel bandwidth is 2 MHz.
A. 12 Mbps
B. 32 Mbps
C. 16 Mbps
D. 24 Mbps
Eplanation
The Correct Answer is D .
Which one of these does not lie in the Link Layer of the TCP/IP Model?
A. IP
B. 802.11
C. DSL
D. SONET
Eplanation
The Correct Answer is A .
IP (Internet Protocol) is a member of the Internet layer.
A pure ALOHA network transmits 200-bit frames on a shared channel of 200 kbps. What is the requirement to make this frame collision-free?
A. 2msec
B. 4msec
C. 2sec
D. 4sec
Eplanation
The Correct Answer is A .
Average frame transmission time
Tfr = 200 bits/200 kbps or 1 ms
Vulnerable time = 2x Tfr = 2 × 1 ms = 2 ms.
Find the checksum byte for the fallowing data words: 10110011, 10101011, 01011010, 11010101
A. 101110101
B. 1110010
C. 1110010
D. 10001101
Eplanation
The Correct Answer is D .
Do binary addition to compute the result.
A device that provides a central connection point for cables is:
A. Gatway
B. Proxy Server
C. Switch
D. Hub
Eplanation
The Correct Answer is D .
Such a device is known as a Hub and is usually used in STAR topologies.
What is the bit rate for high-definition TV (HDTV)?
A. 1.8 Gbps
B. 1.5 Gbps
C. 1.4 Gbps
D. 2 Gbps
Eplanation
The Correct Answer is B .
The HDTV screen is normally a ratio of 16: 9 (in contrast to 4: 3 for regular TV)
There are 1920 by 1080 pixels per screen, and
Screen is renewed 30 times per second.
24-bits represent one color pixel.
Therefore Bit Rate = 1920 × 1080 × 30 × 24 = 1,492992,000 = 1.5 Gbps.
A list of protocols used is known as:
A. protocol stak
B. permutation stack
C. none of the mentioned
D. protocol access
Eplanation
The Correct Answer is A .
A list of the protocols used by a certain system, one protocol per layer, is called a protocol stack.
What is the hamming distance between these 2 codes: 10010010 and 11011001?
A. 2
B. 4
C. 3
D. 6
Eplanation
The Correct Answer is B .
Hamming distance is number of dissimilar bits between 2 streams.
How many layers are there in the OSI reference model?
A. 5
B. 6
C. 7
D. 4
Eplanation
The Correct Answer is C .
The 7 layers are : Physical Layer, Data Link Layer, Network Layer, Transport Layer, Session Layer, Presentation Layer, Application Layer.
UDP stands for ________
A. Undefined Diagnostic Protocol
B. Used Data Protocol
C. Unified Definition Protocol
D. User Datagram Protocol
Eplanation
The Correct Answer is D .
UDP stands for User Datagram Protocol.
2 Half duplex systems can make a Full-Duplex.
A. FALSE
B. TRUE
C.
D.
Eplanation
The Correct Answer is B .
The statement is true.
A pure ALOHA network transmits 200-bit frames on a shared channel of 200 kbps. What is the throughput if the system (all stations together) produces 500 frames per second?
A. 38 frames
B. 146 frames
C. 156 frames
D. 92 frames
Eplanation
The Correct Answer is D .
If the system creates 500 frames per second, or 1/2 frames per millisecond.
Then G = 1/2.
S = G × e−2G = 0.184 (18.4 percent)
This means that
Throughput = 500 × 0.184 = 92
Only 92 frames out of 500 will probably survive
This is the maximum throughput case, percentage-wise.
HTTP stands for ________
A. none of the mentioned
B. Hash Transfer Text Protocol
C. Hash Text Transfer Protocol
D. Hyper Text Transfer Protocol
Eplanation
The Correct Answer is D .
HTTP stands for Hyper Text Transfer Protocol.
Flow Control and Error Control are functions of which layer?
A. Application Layer
B. Network Layer
C. Physical Layer
D. Data Link Layer
Eplanation
The Correct Answer is D .
Flow Control and Error Control are functions of the Data Link Layer.
Which of the following does not lie in the Application Layer of the TCP/IP Model?
A. SMTP
B. UDP
C. HTTP
D. RTP
Eplanation
The Correct Answer is B .
UDP lies in the Transport layer.
Ethernet LANs use which topology?
A. Star
B. Bus
C. Ring
D. Mesh
Eplanation
The Correct Answer is B .
Ethernet LANs use bus topology,
A device that is used to connect a number of LANs is:
A. Switch
B. Router
C. Bridge
D. Repeater
Eplanation
The Correct Answer is B .
A device that is used to connect a number of LANs is a Router
If a periodic signal is decomposed into five sine waves with frequencies of 100, 300, 500, 700, and 900 Hz, what is its bandwidth?
A. 900 Hz
B. can't be determined with the information given
C. 800Hz
D. 2500 Hz
Eplanation
The Correct Answer is C .
The bandwidth is 900-100 = 800 Hz.
Which of the following was the IBM Token bus?
A. IEEE 802.1
B. IEEE 802.11
C. IEEE 802.4
D. IEEE 802.10
Eplanation
The Correct Answer is C .
The IBM Token bus was IEEE 802.4.
SMTP stands for ________
A. Service Message Transmission Permission
B. Secure Message Transfer Protocol
C. Simple Message Transfer Protocol
D. Simple Mail Transfer Protocol
Eplanation
The Correct Answer is D .
SMTP stands for Simple Mail Transfer Protocol.
Which topology has the toughest fault identification?
A. Bus
B. Ring
C. Star
D. Mesh
Eplanation
The Correct Answer is A .
In the bus topology, fault identification is tougher.
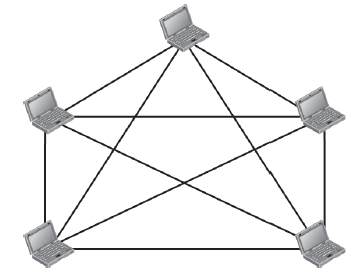
Which network topology does this represent?
In order to prevent a fast sender from swamping a slow receiver with data, feedback is often used. This process is known as:
A. Congestion
B. none of the mentioned
C. Multiplexing
D. Flow Control
Eplanation
The Correct Answer is D .
The process defined above is known as Flow Control.